Several times in the past we have looked at instances where Websense has inappropriately implicated that WordPress was connected to malware infections. In the most recent instance they falsely claimed that a malware infection was only infecting a certain version of WordPress and that there were known vulnerabilities in that version of WordPress. Just a month later they came out with another post that falsely implicated WordPress with another infection. We missed this at the time they put it out because we don’t follow their reporting as it has proven to be so bad. The post was recently brought to our attention and it is worth discussing it now, as what they continue to do is inappropriate and damaging.
This time it began with a posting titled “New Mass Injection Wave of WordPress Websites on the Prowl“, which is a pretty clear implication that the WordPress software had some involvement in the infection. But if you actually read the body of the post you find that they only mention of WordPress is in saying that a “majority of targets are Web sites hosted by the WordPress”. They don’t make any claim of an actual connection between the infection and WordPress. This isn’t a small distinction, as many websites are running WordPress and therefore it would not be unexpected that a more general issue would impact many WordPress based website. (As we will come back to in a little bit, there is also the issue of how accurately Websense measures what software websites are running.) If the issue isn’t related to WordPress than WordPress shouldn’t be emphasized, if mentioned at all, as many people will unnecessarily worry about the security of WordPress. It is quite clear there posting had that effect by looking at the comments on the post and the title of their follow up post “I have the latest WordPress version – is my Website protected?“.
Because Websense provided such little actual information about the malware infection, probably because they didn’t actually have any, it is hard to determine for sure what infection they are referring to and therefore the source. The infection looks to be related to a hack of many Dreamhost based websites, due to Dreamhost’s poor security. That occurred during the same time period, the malware code looks very similar to what we saw with those websites, and the comments on the first post reference that as well. If Websense’s security researchers were actually interested in doing security research, they would have actually investigated what the underlying source of the infections was instead of creating a post that baselessly implicated WordPress as somehow being related to the infections.
We don’t think Websense is intentionally trying to damage WordPress; the reason for doing this appears to get them press coverage. Unfortunately, just as they did with Websense’s last false report, some of press spread this and its non-existent WordPress connection. PCWorld’s article is titled “30,000 WordPress Blogs Infected to Distribute Rogue Antivirus Software” (Websense’s post actually only claimed that a majority of a total “close to 30,000 unique Web sites” were running WordPress) and the WordPress logo is at the top of the article. Dark Readings’ article actually introduces more harmful information to the mix. The article says that a Websense researcher says that “WordPress is so widely used around the world, every version of it is studied and exploited by hackers”, which is highly alarming but not even close to the truth. While there have been a number of security vulnerabilities found and fixed in WordPress in recent years, there haven’t been any that have lead to a major hack of WordPress based websites. That doesn’t mean that there haven’t been targeted attacks using them, though we haven’t seen any reports of that, or that a serious vulnerability couldn’t be found (so make sure you are keeping WordPress updated), but it does mean that running WordPress, as opposed to less popular software, doesn’t put you at some great threat of being hacked.
A Majority of Infected Websites Running WordPress?
The last time Websense brought up WordPress they originally claimed that all of the infected websites they found were not only running WordPress, but that they were all running a specific version of WordPress. When we did our own small analysis of 11 websites that had been listed as infected by Google, we found that 2 of them were currently infected and either not running WordPress or running an older version of WordPress. There were others that also were not running WordPress, but were not infected at the time so we couldn’t independently confirm they had been infected. Based on that data and the fact that they later admitted that the infection was unrelated to WordPress, there data in that instance was at least unrepresentative, if not faulty in some way. The information provided this time doesn’t provide any confidence that they have improved things since then.
In their first post it says that the “majority of targets are Web sites hosted by the WordPress”. A week later in their second post it says that “when we discovered the attack, we found only WordPress sites, and after a week or so, the picture did not change that much” and that “WordPress still serves the majority of the compromised websites; however, we did see a small amount of other CMS as well”. It’s not clear why the second post says that WordPress went from the only thing found to just the majority over a week, when the first post from a week earlier said it was only a majority at that time. There definition of a small amount seems off as well. They say that they found 14 percent were running something other than WordPress, with 10 percent being Joomla and 4 percent being “other”. That is a number far beyond what you would expect if this was truly something related to something in WordPress and had then spread to other parts of websites, which were running WordPress and other some software on different portions of their websites.
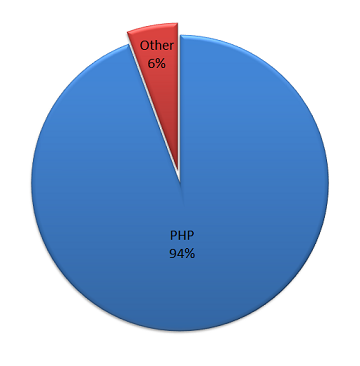
Another piece of their analysis seems even odder. They have a rather odd chart:
The chart shows some use of PHP versus an undefined other. PHP is a scripting language, so this could be a measurement of what language the code powering the website was written in, that website is capable of running PHP code, or maybe something else. The text preceding the chart doesn’t do much to explain what it is measuring or how they measuring it:
We checked several aspects of each of these compromised websites and concluded that most of them are served by Apache webserver and PHP environment. As you can see in the pie chart below, PHP dominates the server side:
Both WordPress and Joomla are written in PHP, so even if all of the “other” were not PHP based you would expect that a measure of either websites written in PHP and websites capable of running PHP code to be 96 percent but on the chart PHP is only 94 percent. One possible explanation of this is that it could be due to some of the websites being served by CDN or some other caching infrastructure, so the underlying server powering the website isn’t measured. Another possibility is that it another example of the poor quality of their measurement infrastructure. Whatever the cause of the discrepancy, it is something that would expect to be explained if they were going to present that chart as part of their analysis.
The larger issue is why they brought up PHP in the first place. Based on the fact that so much web software is written in PHP you would expect that many hacked websites would be using PHP, without the hack having anything to do with that. While there was a recent vulnerability in PHP, found two months after Websense postings, that could lead to websites being hacked some very limited circumstances, PHP isn’t something that is generally going to be the source of the hack. In this case, their data says that six percent of the websites are not using PHP, which would be a pretty good indication that it wasn’t related to PHP. The most likely explanation for highlighting PHP usage, and not many other things, is that they highlighted this finding simply based on PHP high usage among the infected website, without having a reason to believe it is connected to the actual source of the infection. You would hope that a researcher would understand that correlation is not causation, especially in an instance where you would expect there to be a correlation.