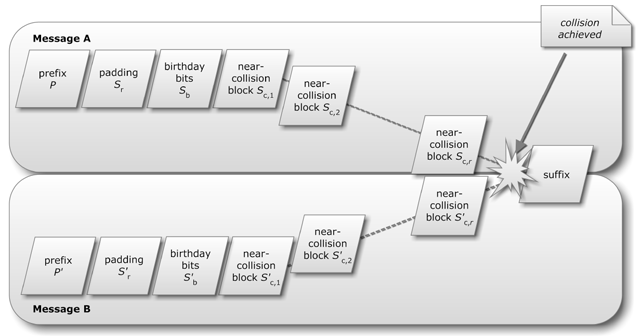
Enlarge / An overview of a chosen-prefix collision. A similar technique was used by the Flame espionage malware that targeted Iran. The scientific novelty of the malware underscored the sophistication of malware sponsored by wealthy nation states.
The dance among blackhat, whitehat, and greyhat hackers grew ever more intricate in 2012, thanks to a steady stream of exploits, vulnerability discoveries, and data breaches. In-the-wild attacks against Internet Explorer, the Java software framework, and other perennial favorites continued, of course. They inflicted plenty of damage on end users, but given their familiarity, they hardly stood out.
What got our attention were attacks on entirely new classes of devices or victims, or in the case of passwords and cryptography, the culmination of new exploit techniques quickly eroding the protection we once took for granted.
From our perspective, here are the five biggest security stories this year.
Read 12 remaining paragraphs | Comments