A researcher has devised a method that reduces the time and resources required to crack passwords that are protected by the SHA1 cryptographic algorithm.
The optimization, presented on Tuesday at the Passwords^12 conference in Oslo, Norway, can speed up password cracking by 21 percent. The optimization works by reducing the number of steps required to calculate SHA1 hashes, which are used to cryptographically represent strings of text so passwords aren't stored as plain text. Such one-way hashes—for example 5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8 to represent "password" (minus the quotes) and e38ad214943daad1d64c102faec29de4afe9da3d for "password1"—can't be mathematically unscrambled, so the only way to reverse one is to run plaintext guesses through the same cryptographic function until an identical hash is generated.
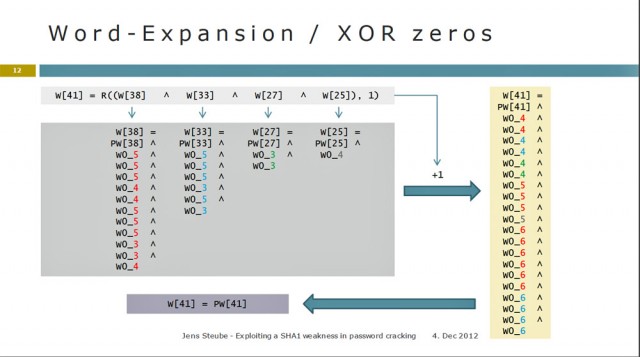
Jens Steube—who is better known as Atom, as the pseudonymous developer of the popular Hashcat password-recovery program—figured out a way to remove identical computations that are performed multiple times from the process of generating of SHA1 hashes. By precalculating several steps ahead of time, he's able to skip the redundant steps, shaving 21 percent of the time required to crack large numbers of passwords. Slides from Tuesday's presentation are here.
Read 10 remaining paragraphs | Comments