Attackers behind a massive espionage malware campaign that went undetected for five years relied in part on a vulnerability in the widely deployed Java software framework to ensnare their victims, a security researcher said.
The unknown attackers infected computers operated by the Russian Federation, Iran, the US, and at least 36 other countries. They used highly targeted malware to collect what's believed to be hundreds of terabytes of sensitive data, according to researchers from antivirus provider Kaspersky Lab. The success of the covert operation is largely the result of malware and phishing e-mails that were highly customized for each victim.
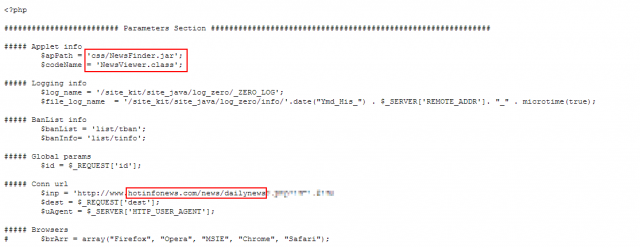
Now, Aviv Raff, CTO of Israel-based Seculert, said he has uncovered a website used to infect some of the victims of Operation Red October (as the campaign has been dubbed). The website exploited a critical Java vulnerability identified as CVE-2011-3544, allowing the attackers to surreptitiously execute malicious code on visitors' computers. Although Oracle developers patched the bug in October of 2011, the malicious Java archive file was compiled the following February.
Read 6 remaining paragraphs | Comments