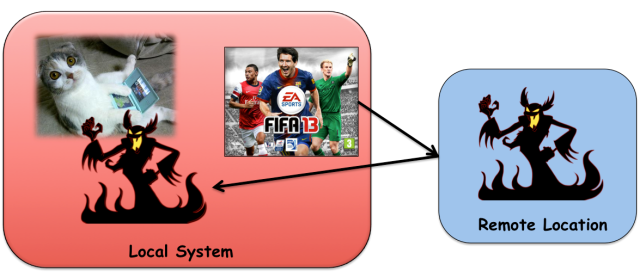
More than 40 million people could be affected by a vulnerability researchers uncovered in EA's Origin online game platform allowing attackers to remotely execute malicious code on players' computers.
The attack, demonstrated on Friday at the Black Hat security conference in Amsterdam, takes just seconds to execute. In some cases, it requires no interaction by victims, researchers from Malta-based ReVuln (@revuln) told Ars. It works by manipulating the uniform resource identifiers EA's site uses to automatically start games on an end user's machine. By exploiting flaws in the Origin application available for both Macs and PCs, the technique turns EA's popular game store into an attack platform that can covertly install malware on customers' computers.
"The Origin platform allows malicious users to exploit local vulnerabilities or features by abusing the Origin URI handling mechanism," ReVuln researchers Donato Ferrante and Luigi Auriemma wrote in a paper accompanying last week's demonstration. "In other words, an attacker can craft a malicious Internet link to execute malicious code remotely on [a] victim's system, which has Origin installed."
Read 5 remaining paragraphs | Comments