Engineers at content delivery network CloudFlare have released open source encryption software that's designed to prevent rogue employees from accessing sensitive information by decrypting data only when two or more people provide keys.
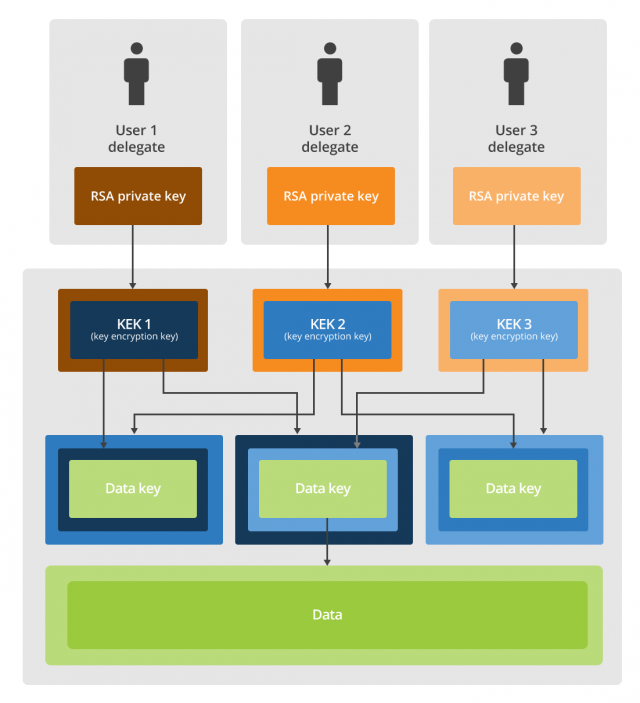
The open source software combines known cryptographic protections with the so-called "two-man rule," which militaries have relied on for decades to prevent the accidental or unauthorized launching of nuclear weapons. Just as armaments of mass destruction can be unleashed only when two authorized service members turn their unique keys at the same time, the data encrypted by the CloudFlare tool can be unlocked only when two or more employees provide passwords that briefly unlock their private cryptographic keys. The software has been dubbed "Red October," a nod to a key scene in the Tom Clancy novel and movie The Hunt for Red October.
The aim of Red October is to fuse trusted cryptographic algorithms with a front-end programming interface that makes them work only when keys possessed by multiple people are presented. It assigns each user a randomly generated 2048-bit RSA key pair. Each user's private key is then encrypted using a separate key based on the 128-bit AES algorithm and a user-chosen password that is cryptographically salted and then stored as a cryptographic hash using the scrypt key derivation function.
Read 3 remaining paragraphs | Comments




