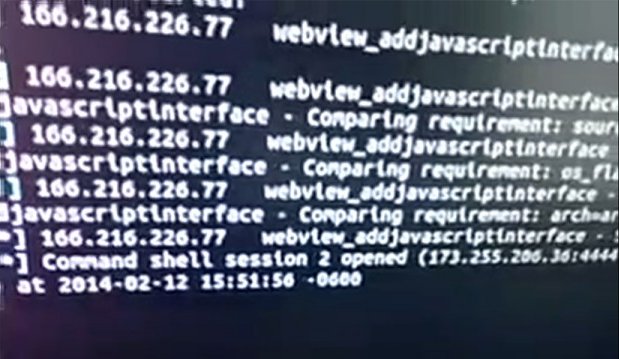
Recently-released attack code exploiting a critical Android vulnerability gives attackers a point-and-click interface for hacking a majority of smartphones and tablets that run the Google operating system, its creators said.
The attack was published last week as a module to the open-source Metasploit exploit framework used by security professionals and hackers alike. The code exploits a critical bug in Android's WebView programming interface that was disclosed 14 months ago. The security hole typically gives attackers remote access to a phone's camera and file system and in some cases also exposes other resources, such as geographic location data, SD card contents, and address books. Google patched the vulnerability in November with the release of Android 4.2, but according to the company's figures, the fix is installed on well under half of the handsets it tracks.
"This vulnerability is kind of a huge deal," Tod Beardsley, a researcher for Metasploit maintainer Rapid7, wrote in a recent blog post. "I'm hopeful that by publishing an E-Z-2-Use Metasploit module that exploits it, we can maybe push some vendors toward ensuring that single-click vulnerabilities like this don't last for 93+ weeks in the wild. Don't believe me that this thing is that old? Just take a look at the module's references if you don't believe me."
Read 4 remaining paragraphs | Comments