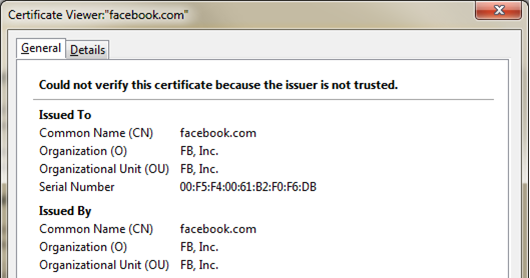
Researchers have found dozens of fake certificates impersonating the secure sections of online banks, e-commerce sites, and social networks. Google, Facebook, iTunes, and even a POP e-mail server belonging to GoDaddy are a small sample of the services affected by the fraudulent credentials, which in some cases can allow attackers to read and modify encrypted traffic passing between end users and protected servers.
The secure sockets layer (SSL) certificates don't pose much of a threat to people using a popular Web browser to visit spoofed websites, because the credentials aren't digitally signed by a trusted certificate authority, researchers from Netcraft wrote in a blog post published Wednesday. They went on to say that people accessing sensitive websites with smartphone apps or other non-browser software may not be so lucky.
They cited several reports published in the past few years that detailed fatal weaknesses in popular software that made it possible for attackers to decrypt encrypted traffic and in some cases impersonate a cryptographically authenticated server. An October 2012 academic study, for instance, uncovered critical defects in a wide-range of applications running on computers and smartphones—some from banks such as Chase and services such as AOL—that failed to check the validity of SSL certificates. A separate study found that Android apps installed on as many as 185 million devices exposed end users' online banking and social networking credentials as well as e-mail and instant-messaging content because the programs used inadequate encryption protections. A more recent report from security firm IOActive uncovered similar weaknesses in apps written for Apple's iOS platform.
Read 5 remaining paragraphs | Comments