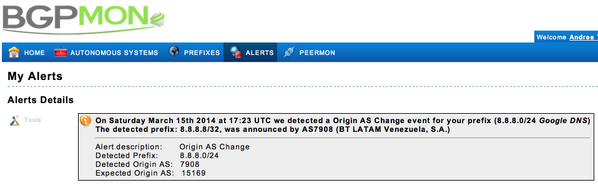
For about a half hour on Saturday, some requests to one of Google’s DNS servers in the US were re-routed through a network in Venezuela. A false Border Gateway Protocol (BGP) announcement from the Venezuelan network caused the diversion, which affected networks primarily in Venezuela and Brazil, as well as a university network in Florida. It all started at 5:23pm Greenwich Time (UTC).
Andree Toonk of the network monitoring service BGPmon.net told Ars that the false routing request was dropped 23 minutes later, “most likely because the network that announced this route realized what happened and rolled back the change (to their router) that caused this.” During the intervening period, he said, traffic may have been re-routed back to Google, or it just may have been dropped. The result was failed DNS requests for those on the affected networks.
Network rerouting through bogus BGP “announcements”—advertisements sent between routers that are supposed to provide information on the quickest route over the Internet to a specific IP address, such as the Google DNS service’s 8.8.8.8—have become increasingly common as a tool for Internet censorship. They're used to stage “man-in-the-middle” attacks on Web users and to passively monitor traffic to certain domains.
Read 6 remaining paragraphs | Comments