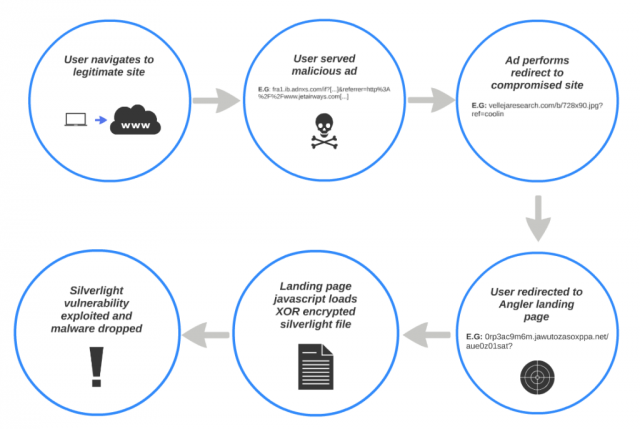
The number of drive-by malware attacks that exploit vulnerabilities in Microsoft's Silverlight application framework may be surpassing those that abuse Oracle's Java framework, according to a recent analysis of one popular hack-by-numbers tool kit.
Since April 23, the Angler exploit kit has shown a significant uptick in attacks that target Silverlight users, according to a blog post published Monday by Levi Gundert, technical lead in Cisco Systems' threat research group. While the Silverlight exploits were accompanied by attacks that also targeted Adobe's Flash player, the recent campaign failed to trigger vulnerabilities in Oracle's Java framework, which over the past couple of years, has become widely targeted by malicious hackers who surreptitiously install malware by exploiting vulnerable software on end users' computers.
To succeed, the Angler campaign observed by Gundert had to exploit two Silverlight vulnerabilities, one that Microsoft patched 14 months ago and the other that was fixed in October. CVE-2013-0074 gave attackers the ability to remotely execute malicious code, while CVE-2013-3896 provided the means to bypass data execution prevention, a security mitigation added to most Microsoft applications in recent years. The measure prevents most data loaded into memory from being executed.
Read 2 remaining paragraphs | Comments