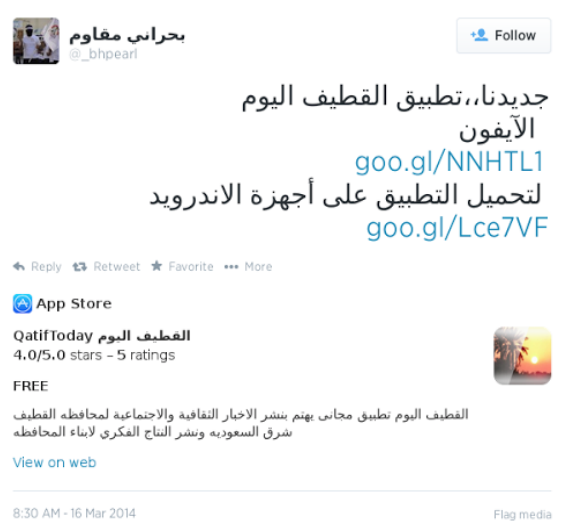
On Twitter, it was billed as Qatif Today, a legitimate Android app that provides news and information in Arabic with a focus on the Qatif governorate of Saudi Arabia. But in fact, the shortened link came with a hidden extra—an advanced trojan wealthy nation states use to spy on criminal suspects and political dissidents.
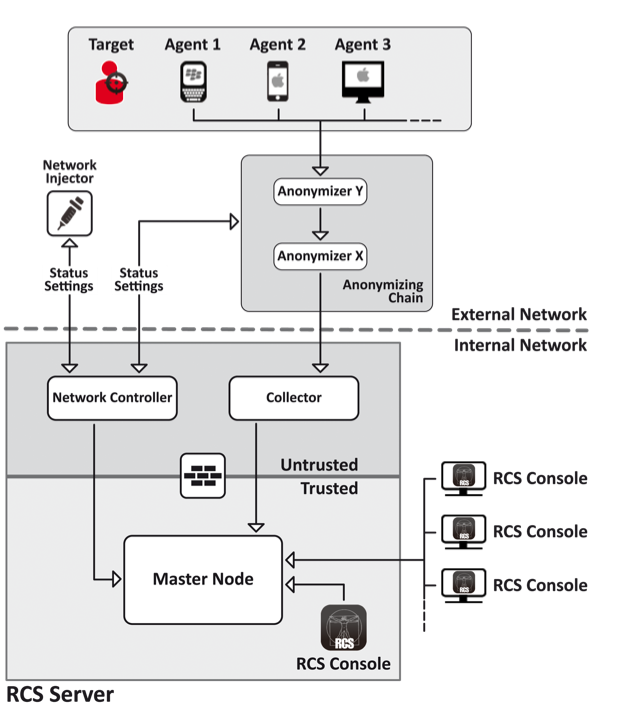
Citizen Lab, the University of Toronto group that monitors government surveillance in the digital age, analyzed the recently discovered instance of the fake Qatif Today app in a blog post headlined Police Story: Hacking Team’s Government Surveillance Malware. The account provides a rare glimpse into malware developed by "Hacking Team," a highly secretive outfit based in Italy that charges governments top dollar for extremely stealthy spyware that's often referred to as a "lawful intercept" program.
The trojan is known as an Android implant because it cloaks itself inside a legitimate third-party app. People who are infected with it must first be tricked into obtaining the Android installation package (APK) from a non-authorized source, which in this case was this now-shuttered Dropbox location. Aside from that, victims may have little indication anything is amiss. To lend it legitimacy, the malicious APK was signed by a digital certificate that appeared to be related to Java and its original creator Sun Microsystems. Citizen Labs identified six other samples signed by the same certificate.
Read 8 remaining paragraphs | Comments