Large numbers of home and small-office routers are under the control of hackers who are using them to overwhelm websites with more junk traffic than they can handle, security researchers said Tuesday. The devices are so poorly secured that they have given rise to self-perpetuating botnets commandeered by multiple attackers.
The distributed denial-of-service attacks have been underway since at least December and show no signs of letting up, researchers from DDoS-protection firm Incapsula said. Over the past four months, Incapsula has recorded attacks from 40,269 IP addresses belonging to 1,600 ISPs around the world. All of the compromised routers observed were able to be remotely administered, and almost all of those accounts continued to use vendor-provided login credentials. Incapsula found that the devices were infected by a variety of malware titles, including MrBlack, Dofloo, and Mayday. The ease of compromising the routers makes them free for the taking, all but ensuring an unending series of follow-on attacks. The researchers wrote:
Given how easy it is to hijack these devices, we expect to see them being exploited by additional perpetrators. Even as we conducted our research, the Incapsula security team documented numerous new malware types being added—each compounding the threat posed by the existence of these botnet devices.
Self-sustaining Botnets
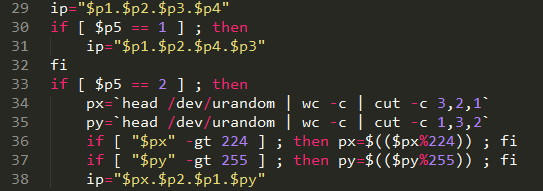
Our analysis reveals that miscreants are using their botnet resources to scan for additional misconfigured routers to add to their “flock.” They do so by executing shell scripts, searching for devices having open SSH ports which can be accessed using default credentials.
This script identifies remotely accessible routers so they can be hijacked and made part of a botnet.IncapsulaFacilitating the infiltration, all of these under-secured routers are clustered in the IP neighborhoods of specific ISPs, that provide them in bulk to end-users. For perpetrators, this is like shooting fish in a barrel, which makes each of the scans that much more effective. Using this botnet also enables perpetrators to execute distributed scans, improving their chances against commonplace blacklisting, rate-limiting and reputation-based defense mechanisms.
The proliferation of poorly designed routers and inexperienced Internet users are the two most crucial ingredients fueling the self-perpetuating botnets. Manufacturers design their routers to be easily connected by giving each one the same administrator username and password and in some cases making the devices open to remote administration by default rather than allowing remote administration only when a user turns it on. The manufacturers frequently include no documentation warning users to change the default credentials, and even when those warnings are included, many end users don't heed the advice.
Read 3 remaining paragraphs | Comments