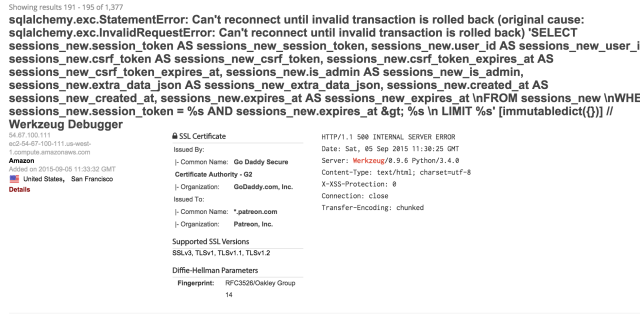
Enlarge / Results of a Shodan search performed on September 11 made it clear Patreon was vulnerable to code-execution attacks. (credit: Detectify)
Five days before Patreon.com officials said their donations website was plundered by hackers, researchers at a third-party security firm notified them that a serious programming error could lead to disastrous results. The researchers now believe the vulnerability was the entry point for attackers who went on to publish almost 15 gigabytes' worth of source code, user password data, and private messages.
The error was nothing short of facepalm material. Patreon developers allowed a Web application tool known as the Werkzeug utility library to run on its production servers. Specifically, according to researchers at Swedish security firm Detectify, one or more of Patreon's live Web apps—that is, the same Web apps real users relied on when visiting the real site—was running Werkzeug debugging functions. A simple query on the Shodan search service brought the goof to the attention of Detectify researchers, who in turn notified Patreon officials on September 23. Adding to their concern, the same Shodan search shows thousands of other websites making the same game-over mistake.
Remote code execution by design
The reason for the alarm was clear. The Werkzeug debugger allows visitors to execute code of their choice from within the browser. Werkzeug developers have long been clear about this capability and the massive risks that stem from using it in production environments. But in case anyone missed the warning, an independent blogger called attention to the threat last December.