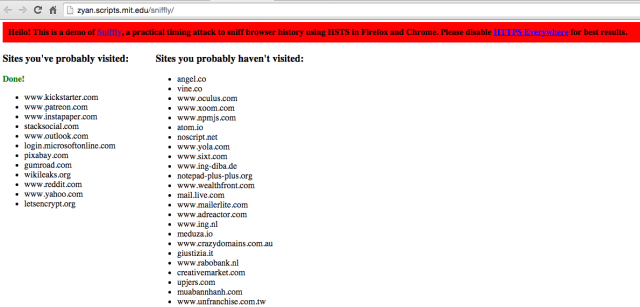
Enlarge (credit: Yan Zhu)
Over the past decade, there's been a privacy arms race between unscrupulous website operators and browser makers. The former wield an ever-changing lineup of so-called zombie cookies that can't be easily deleted and attacks that sniff thousands of previously visited sites, while browser makers aim to prevent such privacy invasions by closing the design weaknesses that make them possible. Almost as soon as one hole is closed, hackers find a new one.
Over the weekend, a researcher demonstrated two unpatched weaknesses that Web masters can exploit to track millions of people who visit their sites. Taken together, the attacks allow websites to compile a list of previously visited domains, even when users have flushed their browsing history, and to tag visitors with a tracking cookie that will persist even after users have deleted all normal cookies. Ironically, the techniques abuse relatively new security features that are already built into Google Chrome and Mozilla Firefox and that may make their way into other mainstream browsers in the future.
The history-sniffing attack works against people who visit sites that use HTTP strict transport (HSTS). The specification allows websites to instruct browsers to connect only when an encrypted HTTPS connection is available and to reject any attempts to use an unsecured HTTP link. The measure, which is used by banks, cloud services, and other sensitive sites, is designed to prevent downgrade attacks, in which a hacker with the ability to tamper with traffic passing between an end user and server resets an HTTPS connection to use HTTP so the data isn't protected against snooping or modification.