Sign up to extort hapless Windows users over Tor for mere Bitcoins a month! (credit: Malware, based on Node.js desktop framework, offered up to would-be extortionists for fee.)
Malware researchers at the anti-virus company Emisoft have uncovered a new "ransomware" package that encrypts the files of victims and demands payment to restore them. Dubbed Ransom32, the malicious code is different from CryptoWall and many other previous ransomware variants in two key ways: it was coded using JavaScript, and it’s being offered to would-be cybercriminals as a paid service.
In a blog post, Emisoft Chief Technology Officer Fabian Wosar described the malware and its Tor-based administrative Web interface. Users of the service log in with their Bitcoin wallet addresses; once they're connected, they can configure features of the malware "client" for the service such as the messages displayed to victims during the malware installation and how much to demand in ransom for encryption keys. They can also track the payments already made and how many systems have become infected.
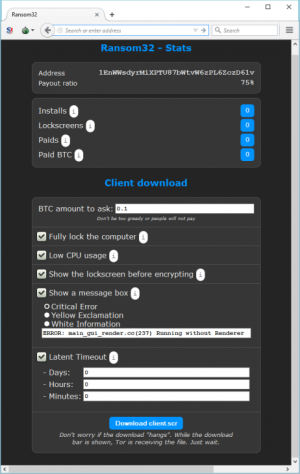
The Tor-based control panel for configuring Ransom32. Just click a few boxes, add some text, and you're ready to extort. (credit: Emsisoft)
The malware itself is based on NW.js, a framework based on Node.js that allows developers to write Windows applications in JavaScript. It is delivered, renamed as "chrome.exe," in a self-extracting archive along with a Tor client (renamed as "rundll32.exe") and a set of Visual Basic scripts used to display customized pop-up alert messages and perform some basic file manipulation. The malware is also packaged with a renamed version of the Optimum X Shortcut utility—software used to create and change Start menu items and desktop shortcuts. The entire payload is over 22 megabytes, which is huge in comparison to other crypto-ransomware packages.