(credit: Lawrence Abrams, BleepingComputer)
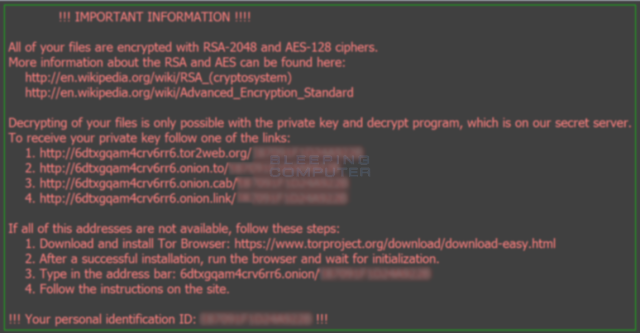
Several security researchers have discovered a new type of malware that jumps onto the ransomware bandwagon, encrypting victims' files and then demanding a payment of half a bitcoin for the key. Named "Locky," the malware depends on a rather low-tech installation method to take root in a user's system: it arrives courtesy of a malicious macro in a Word document.
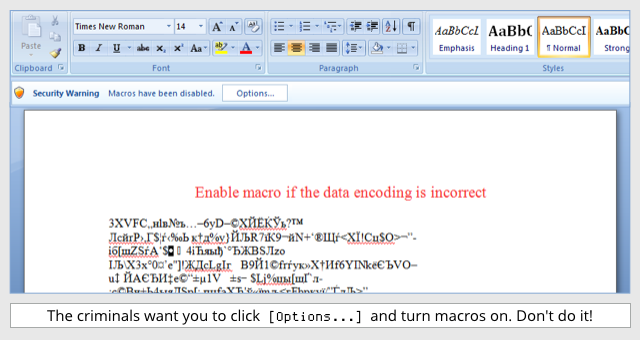
Security researchers Kevin Beaumont and Lawrence Abrams each wrote an analysis of Locky on Tuesday, detailing how it installs itself and its components. The carrier document arrives in an e-mail that claims to be delivering an invoice (with a subject line that includes an apparently random invoice number starting with the letter J). When the document is opened, if Office macros are turned on in Word, then the malware installation begins. If not, the victim sees blocks of garbled text in the Word document below the text, "Enable macro if the data encoding is incorrect"—and then infects the system if the user follows that instruction.
Somehow, this malware has already infected hundreds of computers in Europe, Russia, the US, Pakistan, and Mali. The malicious script downloads Locky's malware executable file from a Web server and stores it in the "Temp" folder associated with the active user account. Once installed, it starts scanning for attached drives (including networked drives) and encrypts document, music, video, image, archive, database, and Web application-related files. Networked drives don't need to be actively mapped to be found, however.