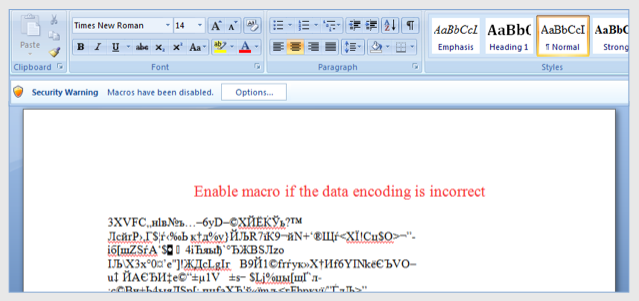
In the late 1990s, Microsoft Office macros were a favorite vehicle for surreptitiously installing malware on the computers of unsuspecting targets. Microsoft eventually disabled the automated scripts by default, a setting that forced attackers to look for new infection methods. Remotely exploiting security bugs in Internet Explorer, Adobe Flash, and other widely used software soon came into favor.
Over the past two years, Office Macros have made a dramatic comeback that has reached almost a fevered pitch in the past few months. Booby-trapped Excel macros, for instance, were one of the means by which Ukrainian power authorities were infected in the weeks or months leading up to December's hacker-caused outage that affected 225,000 people. "Locky," a particularly aggressive strain of crypto ransomware that appeared out of nowhere two weeks ago, also relies on Word macros. The return of the macro-delivered malware seemed to begin in late 2014 with the advent of a then-new banking trojan called Dridex.
The return of the macro may have been a reaction to security improvements that Adobe, Microsoft, and Oracle have made to their software. Not only were the companies patching dangerous bugs more quickly, but in many cases, they fortified their code with defenses that caused exploits to simply crash the application rather than force it to execute malicious code. Streamlined update mechanisms and greater end user awareness about the importance of installing security patches right away may also have made code-execution exploits to fall out of favor.