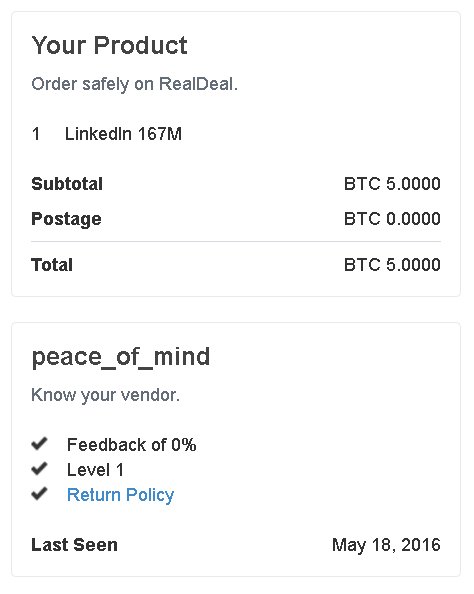
Login credentials for as many as 117 million LinkedIn accounts have been put up for sale online by someone who is seeking more than $2,200 for the haul, a security researcher said.
The credentials—which include e-mail addresses and passwords hashed using the woefully weak SHA1 function—appear to come from a 2012 breach of the career networking site, researcher Troy Hunt said in a series of tweets. LinkedIn officials have since verified that the 2012 hack was the source and said they are working to invalidate any passwords that may still be actively used on compromised accounts. According to LeakedSource, a site that maintains a database of more than 1.25 billion compromised accounts, the new batch contains data for 167 million accounts. 117 million of the records in the batch include a password field.
The discovery means that the 2012 LinkedIn breach was much bigger than previously believed. At the time, researchers found almost 6.5 million credentials belonging to site users. It's not clear if the new number of affected accounts is news to LinkedIn. In the days following discovery of the 2012 breach, company officials implemented a mandatory password reset for affected users. A statement from company officials on Wednesday saying that they're working to change any passwords still in use leaves open the possibility that they were unaware the number was so high.