(credit: Duo Security)
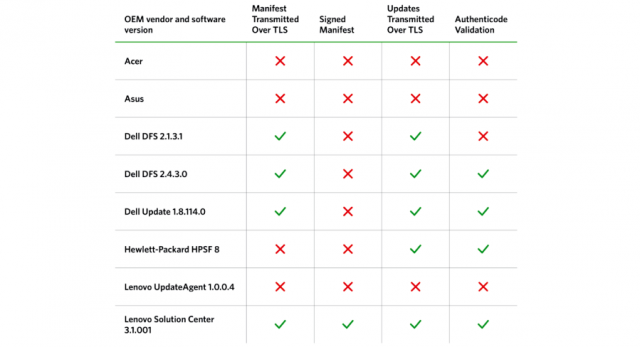
The next time you're in the market for a new Windows computer, consider this: if it comes from one of the top five manufacturers, it's vulnerable to man-in-the-middle attacks that allow hackers to install malware.
That's the take-away from a report published Tuesday by researchers from two-factor authentication service Duo Security. It found third-party updating tools installed by default threatened customers of Dell, HP, Lenovo, Acer, and Asus. The updaters frequently expose their programming interfaces, making them easy to reverse engineer. Even worse, the updaters frequently fail to use transport layer security encryption properly, if at all. As a result, PCs from all five makers are vulnerable to exploits that allow attackers to install malware.
"Hacking in practice means taking the path of least resistance, and OEM software is often a weak link in the chain," the Duo Security report stated. "All of the sexy exploit mitigations, desktop firewalls, and safe browsing enhancements can't protect you when an OEM vendor cripples them with pre-installed software."