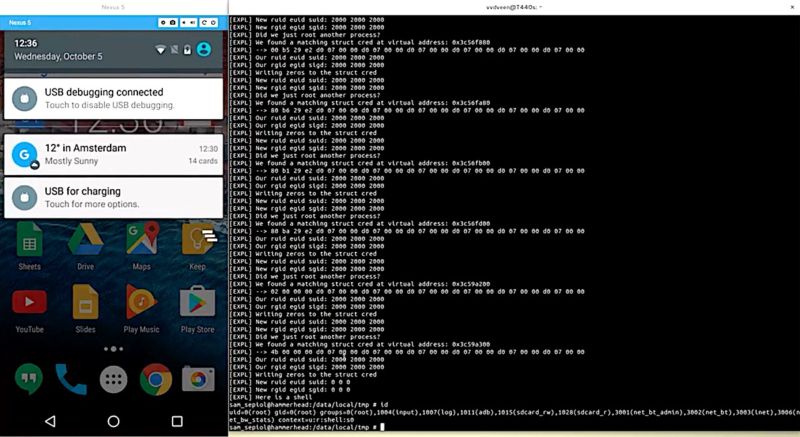
Enlarge / An LG Nexus 5 at the moment it is rooted using Rowhammer-induced bit flips. (credit: van der Veen et al.)
Researchers have devised an attack that gains unfettered "root" access to a large number of Android phones by exploiting a relatively new type of bug that allows adversaries to manipulate data stored in memory chips.
The breakthrough has the potential to make millions of Android phones vulnerable, at least until a security fix is available, to a new form of attack that seizes control of core parts of the operating system and neuters key security defenses. Equally important, it demonstrates that the new class of exploit dubbed Rowhammer can have malicious and far-reaching effects on a much wider base of devices than was previously known, including those running ARM chips.
Previously, some experts believed Rowhammer attacks that altered specific pieces of security-sensitive data weren't reliable enough to pose a viable threat because exploits depended on chance hardware faults or advanced memory-management features that could be easily adapted to repel the attacks. Now, an international team of academic researchers is challenging those assumptions by demonstrating a Rowhammer exploit that alters crucial bits of data in a way that completely roots name brand Android devices from LG, Motorola, Samsung, OnePlus, and possibly other manufacturers. An app containing the researchers' rooting exploit requires no user permissions and doesn't rely on any vulnerability in Android to work.