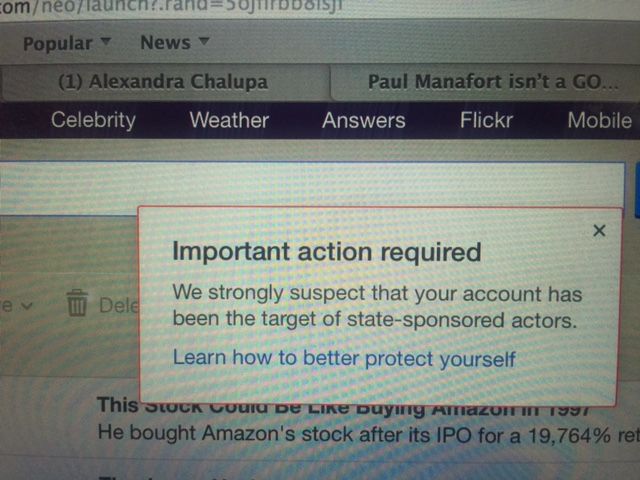
An image sent by DNC staffer Alexandra Chalupa shows a warning message she received from Yahoo Mail. She may have been targeted using data from one of the Yahoo breaches or a forged cookie based on stolen Yahoo code. (credit: Alexandra Chalupa)
In October of 2013, as a result of documents leaked by Edward Snowden, we learned the National Security Agency tapped straight into the connections between data centers at Yahoo and Google as part of a program called MUSCULAR. A month later, Yahoo announced it would encrypt all of its internal networks between data centers and add Secure Socket Layer encryption and secure (HTTPS) Web connections to all its services.
That move, however, failed to prevent two major breaches of user data: a breach affecting user data from more than 500 million user accounts late in 2014 (revealed in September) and the breach revealed yesterday involving data from more than 1 billion accounts. The recent break took place in August of 2013—before the barn door was closed. In addition, Yahoo's chief information security officer, Bob Lord, said that the parties behind the 2014 breach had stolen some of Yahoo's code and used it to forge Web "cookies" that gave access to users' accounts without the need to use login credentials.
Evidence of the August 2013 breach was given to Yahoo by "law enforcement officials," according to Lord, but it was likely discovered by a security researcher watching for data on underground markets. That suggests the data was in circulation in underground marketplaces in one form or another and actively in use by Internet criminal rings for a variety of purposes. If that's the case, then practically all of Yahoo's users who set up accounts prior to 2013 may have had details from their accounts used in targeted attacks, attempts to gain access to other Web accounts and cloud services, or any number of other scams.